Forum tip: Always check when replies were posted. Technology evolves quickly, so some answers may not be up-to-date anymore.
-
 Julia
4Access and secret keys are one of the way you connect to Amazon S3 as a IAM user. You can contact your manager/responsible person who has a master account and granted you the access and secret keys to find out your IAM policy and whether it is an option for you to extend your permissions.
Julia
4Access and secret keys are one of the way you connect to Amazon S3 as a IAM user. You can contact your manager/responsible person who has a master account and granted you the access and secret keys to find out your IAM policy and whether it is an option for you to extend your permissions. -
 Julia
4If you are master account, you can use IAM Manager to create as many IAM users as you want with different permissions. There you can also generate access and secret keys for those IAM users and, finally, use IAM users access/secret keys for different purposes that you have.
Julia
4If you are master account, you can use IAM Manager to create as many IAM users as you want with different permissions. There you can also generate access and secret keys for those IAM users and, finally, use IAM users access/secret keys for different purposes that you have. -
 slpelts
0I have cloudberry explorer sorry
slpelts
0I have cloudberry explorer sorry
I have several buckets. I have different websites that i am going to store data in based on website as to which bucket it goes.
I am currently using keypair for master user, ME,
I would like to have different keypair for the different buckets
plus prefer that the websites using s3 SDK only have read/write permissions
again thanks.
i have dealt with windows server permissions but this is crazy newAttachment cloudberry iam error
(47K)
cloudberry iam error
(47K)
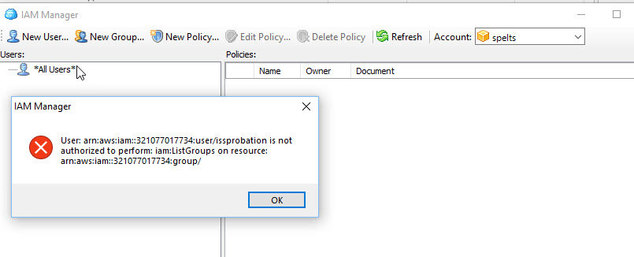
-
 Julia
4You can register your master Amazon S3 account in CloudBerry Explorer and configure any IAM user that you want.
Julia
4You can register your master Amazon S3 account in CloudBerry Explorer and configure any IAM user that you want.
If you need those IAM users be able to use IAM manager as well, you should grant them required permissions (i.e. "iam:*").
If you would like those IAM users be able to access certain buckets only, so you can grant them full access for those buckets and no need for "iam" permissions then.
Welcome to MSP360 Forum!
Thank you for visiting! Please take a moment to register so that you can participate in discussions!
Categories
- MSP360 Managed Products
- Managed Backup - General
- Managed Backup Windows
- Managed Backup Mac
- Managed Backup Linux
- Managed Backup SQL Server
- Managed Backup Exchange
- Managed Backup Microsoft 365
- Managed Backup G Workspace
- RMM
- Connect (Managed)
- Deep Instinct
- CloudBerry Backup
- Backup Windows
- Backup Mac
- Backup for Linux
- Backup SQL Server
- Backup Exchange
- Connect Free/Pro (Remote Desktop)
- CloudBerry Explorer
- CloudBerry Drive
More Discussions
- Error: The underlying connection was closed: Could not establish trust relationship for the SSL/TLS
- Assuming an IAM Role via CloudBerry Explorer - a server connection error
- Error occurred during backup: You are not authorized to perform selected operation.
- Backups are failing with "connection was forcibly closed by the remote host" error
- Terms of Service
- Useful Hints and Tips
- Sign In
- © 2026 MSP360 Forum






