Forum tip: Always check when replies were posted. Technology evolves quickly, so some answers may not be up-to-date anymore.
-
Enabling Compliance Mode Immutable BackupsSelected month is the beginnning of the yearly period. So we should keep one full Y backup for period December - November.
If you have started a backup on the 31th of October - it creates new Y backup on that day (first sucessful backup for period December 2022 - November 2023). A backup created after 1st of December will be the next Y backup for December 2023 - November 2024.
GFS scheme is described here:
https://help.msp360.com/cloudberry-backup/backup/about-backups/gfs/gfs
https://help.msp360.com/cloudberry-backup/backup/about-backups/gfs/gfs-faq -
Enabling Compliance Mode Immutable BackupsHi,
I have check with the latest build 7.9.1.128
Object lock should be enabled for storage account and in plan.
You should remove this from enginesettings for your S3 connection:
<ImmutabilityMode xsi:nil="true" />
and replace with
<ImmutabilityMode>COMPLIANCE</ImmutabilityMode>
Then restart the App.
In case you are using master password, the warning will appear
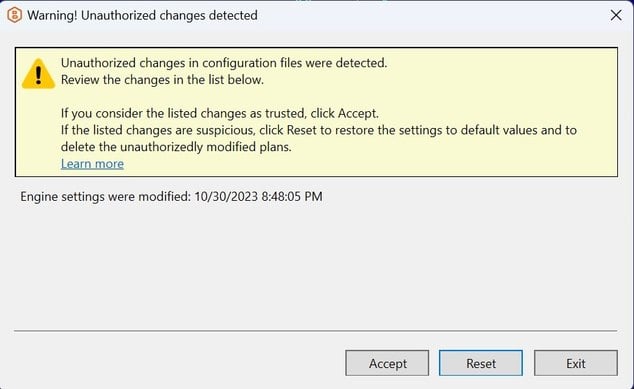
Accept changes.
Run the plan.
If successful GFS backup was created, all data parts (*.cbl files) should be protected with object lock.
You can check this will CloudBerry Explorer:
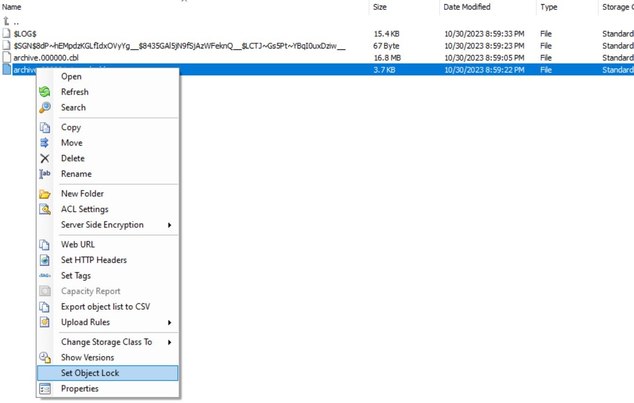
Object lock
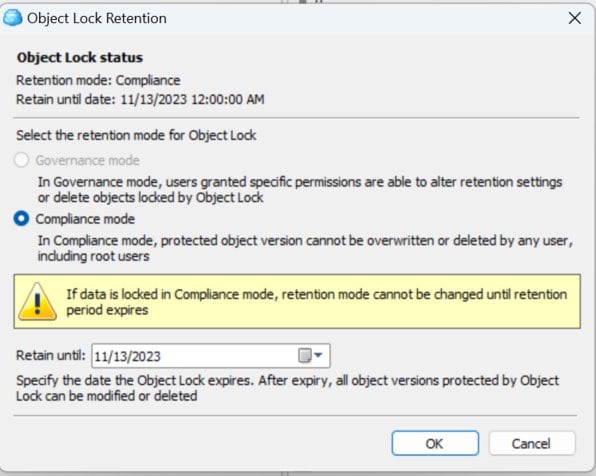
Object headers
-
CloudBerry Backup 7.4 BETA
Hi Yuri,
Please use Tools->Diagnostic in the product to send us logs&suggestions.
Please add "7.4 Beta" to the message to address dev/PM teams.
You can also report here ;-)
Thanks! -
Group report for plan contents and schedulesHi!
Please check RMM->Remote management
Group action button on the right
Plan settings report -
.NET HttpClient issuesHi, !
We are not using HttpClient. Currently, we have no plans on moving the drive product to .net core.
Please describe your case.
What does "issues" mean?
What files do you have under the drive directory, how are they changing?
Please send logs from the product to support and mention this thread on the forum.
Thank you! -
Backup doesn't backup files with different character cases!!??
Probably you need cross-region replication, promised by Wasabi in October 2018?
AV, dev team -
Realtime backup only during specific time period?
Probably you just need to limit bandwidth?
You can set limit for business hours in Tools->Options->Bandwidth. -
Changing between single to hybrid back-up
We are working on improving hybrid mode for future releases (I expect this in 2-3 month), it will be possible to enable hybrid mode in plan, this will upload only required files locally and required to the cloud, currently new hybrid plan reuploads everything to local storage at first and then uploads to cloud.
You can restore directly from cloud, no need to use hybrid location.
The main idea of hybrid backup - reduce loading of your production servers, disks are accessed only once and reading is quick (assuming local backups are performed with better bandwidth). -
Remove local location from Backup Storage tabYou have to delete unused account.
Go to left menu item->Edit accounts and delete your local account. -
CloudBerry Backup Ultimate 5.9?
We have tried to reproduced, backup and restore was successful.
1. Share folder on windows 2012
2. Create folder from mac pc and assign image. Icon\r files are created.
3. Backup from windows agent was successful
4. Restore from windows agent was also successful
5. Restored folder's image is not displayed correctly, need to dig more in that, but files are created as in original folder.
What is your concern? -
CloudBerry Backup Ultimate 5.9?
Please describe your use case.
You have NFS share on mac, that you back up by Windows Backup from another PC ?
Thanks -
Refreshing Storage TabNeed logs and probably repository.
Repository sync and consistency check may lock database. -
Backing up same files repeatedlyPlease provide ticket id.
Hybrid backup currently copies all files backed up locally to cloud destination.
If you deselect files, previously backed up locally files should go to cloud in any case.
Newly created hybrid plan will make another backup of all files to local destination and then will move them to cloud.
We plan to redesign this in future if there are many customers requests. -
Backups failing w/ 'remote name could not be resolved'
No matter start manually or by schedule.
Maybe you are running different backup plans.
Correct dns name should be ws.mspbackups.com
Please send logs to support team, this makes things clear for us -
install optionsPlease provide details if you need custom rebranding for different companies (includes splash, icons, wizard images) or it is about options like allow console, allow transfer acceleration, restore to ec2, etc.
We plan to split these in future. New images requires new build, but options can be updated on the fly. -
Problem with Minio SSLYour private key should be generated with elliptic curve. This is prior CSR step.
-
Problem with Minio SSLHi Jacky,
I have investigated this a little bit.
The issue depends on server and client cipher suites. The same version should be allowed/available on both sides otherwise TLS channel will not be established.
I have look on minio on windows server 2008 installation.
These cipher are availble by default.
TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
And these only in case elliptic curve method is used for generating certificate.
TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
If you use self signed ssl certificate, you can regenerate it with elliptic curve method.
Probably you can also ask for such cetificate from the public authority.
Windows 7 client.
We use native client and there is only ECDSA AES-GCM ciphers in common.
No updates available for extending the list.
Browsers (Chrome and Firefox) use ChaCha20-Poly1305 ciphers, that are not included in windows client.
Known workaround for Windows 7 - update minio server certificate.
Windows 10 client
RSA authentication method available, so everything will run smoothly.
Please tell what is your environment (server/client)?
Probably there is an easy way to extend list of ciphers on minio server side, hasn't looked yet. -
Attempting to Write Oversized MFT RecordHi!
Please increase destination disk, this should help.
Seems there is minimum disk requirements calculation issue, we need to investigate.
This is not frequent issue, send us logs please using Tools->Diagnostic from the product and add message with link to that thread.
Thanks




